MITRE ATT&CK is a designed representation / model /
guide which helps to understand cyber adversarial behavior TTPs – tactics
(initial intrusion), techniques (ways they use) and procedures (what method
/common knowledge they employ to make attack successful). MITRE ATT&CK
itself stands for MITRE adversarial tactics, techniques, and common knowledge. MITRE
displays how cyber attacks and intrusions happens in real threat.
MITRE exposes all various adversary attack lifecycle and
platforms / systems / assets they are known to target. It has knowledge base of
all APT groups which basically reveals how these APT groups target end users /
systems and what is the method they use to perform attack i.e., what are the
data sources or techniques they employ. Also, MITRE helps on mitigation of
these attacks.
MITRE helps offensive (red team) to emulate specific threats
based on adversary behavior which helps to bridge the gaps in visibility,
defensive tools, and countermeasure or process in place – and close them. MITRE
also helps to enhance security posture against specific adversary behavior
(techniques they use). So, this strategy well aligns defenses against adversaries.
It was released in 2014. MITRE and ATT&CK came with this
framework based on military kill chain methodology which is F2T2EA kill chain
model. F2T2EA stands for Find, Fix, Track, Target, Engage, and Access.
It was also known to have 4F’s in previous terminology.
4 F’s –
1.
Find the enemy
2.
Fix the enemy
3.
Fight the enemy
4.
Finish the enemy
MITRE ATT&CK closely follows cyber kill chain
methodology which have seven phases – given by Lockheed Martin. Lockheed Martin
is an American corporation which looks into various areas like aerospace, arms,
information security, defense and technology.
1.
Reconnaissance
2.
Weaponization
3.
Delivery
4.
Exploitation
5.
Installation
6.
Command and Control
7.
Actions on objectives
MITRE ATT&CK has a database of enterprise (Windows, Linux,
macOS, Containers, Cloud and Networks / mobile (Android or iOS) / ICS (Industrial
control system) matrices, tactics, techniques and mitigations.
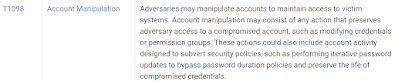
Each Tactics has been given a unique ID which shows why
an adversary is trying to use a technique or sub-technique. What is their
overall goal of using that tactic? So, it gives Tactic ID, Name of Tactic and a
short description.
Similarly, each technique also has been given a unique ID,
Name and how adversary is achieving the overall goal (which was decided in
tactic).
In the end we have a mitigation strategy which helps on
closing the attack vector / path that an adversary is employing. We have an ID,
Name and Description on how to mitigate attack vector.
MITRE ATT&CK framework is in a constant state of development
which always keep adding new information and threat intel to extend the
knowledge base.
Any org. can make use of MITRE ATT&CK framework to assess
their security posture and defensive mechanism in place against various APT
groups and adversaries who uses different attack lifecycle on certain platforms.
MITRE ATT&CK framework can be integrated with different tools and using
regex (regular expressions) we can also play around a bit combining different techniques
and sub-techniques layer of multiple APT groups to see what is the common methodology
they are using.
Regex are special string characters which helps to see
patterns using different search operations (i.e., operators, characters, and
other constructs).
Hope this article at least gives an introductory view to understand
MITRE ATT&CK framework. If so, please leave your comments below.
Mentioning some links that can be referred to learn more
about MITRE ATT&CK Framework:
·
https://attack.mitre.org/matrices/enterprise/
- MITRE ATT&CK Matrices
·
https://attack.mitre.org/tactics/enterprise/
- MITRE ATT&CK Tactics
·
https://attack.mitre.org/techniques/enterprise/
- MITRE ATT&CK Techniques and Sub-techniques
·
https://attack.mitre.org/mitigations/enterprise/
- MITRE ATT&CK Mitigations
·
https://attack.mitre.org/resources/
- MITRE ATT&CK Resources (Whitepapers, articles, and PDFs)
·
https://attack.mitre.org/groups/
- MITRE ATTACK Adversary Groups
· https://en.wikipedia.org/wiki/ATT%26CK - Wikipedia article on MITRE ATT&CK
· https://en.wikipedia.org/wiki/Kill_chain#Cyber - Wikipedia article on Cyber Kill Chain Model
·
https://en.wikipedia.org/wiki/Lockheed_Martin
- Wikipedia article on Lockheed Martin Corporation
·
https://attack.mitre.org/software/
- MITRE ATT&CK common software, utilities and tools
·
https://mitre-attack.github.io/attack-navigator/
- MITRE ATT&CK navigator to use regex
·
https://medium.com/mitre-attack
- MEDIUM articles on MITRE ATT&CK








No comments:
Post a Comment